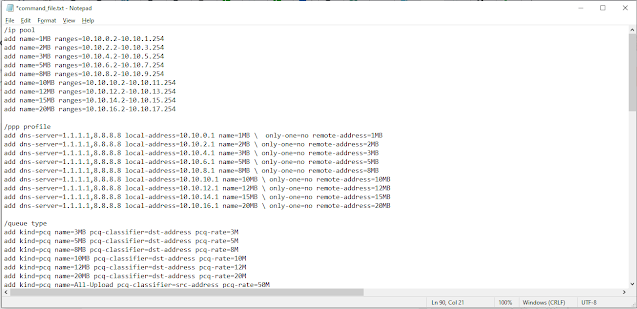
Fast and Speedtest reday script
/ip firewall address-list
add address=10.0.0.0/8 list=Client-IP
add address=103.103.42.0/24 list=Fast-Speedtest
add address=103.125.178.0/24 list=Fast-Speedtest
add address=42.201.253.0/24 list=Fast-Speedtest
add address=103.135.44.0/24 list=Fast-Speedtest
add address=118.107.138.0/24 list=Fast-Speedtest
add address=103.113.100.0/24 list=Fast-Speedtest
add address=203.135.29.0/24 list=Fast-Speedtest
add address=115.167.73.0/24 list=Fast-Speedtest
add address=202.69.12.0/24 list=Fast-Speedtest
add address=58.65.177.0/24 list=Fast-Speedtest
add address=103.55.68.0/24 list=Fast-Speedtest
add address=58.65.171.0/24 list=Fast-Speedtest
add address=103.12.198.98 list=Fast-Speedtest
add address=182.176.176.0/24 list=Fast-Speedtest
add address=119.30.107.0/24 list=Fast-Speedtest
add address=115.186.185.0/24 list=Fast-Speedtest
add address=23.246.54.0/23 list=Fast-Speedtest
add address=54.154.202.0/23 list=Fast-Speedtest
add address=45.57.50.0/23 list=Fast-Speedtest
add address=198.38.114.0/23 list=Fast-Speedtest
add address=103.15.246.3 list=Fast-Speedtest
add address=151.101.10.219 list=Fast-Speedtest
add address=23.74.247.112 list=Fast-Speedtest
add address=103.15.40.4 list=Fast-Speedtest
add address=203.76.99.30 list=Fast-Speedtest
add address=103.58.73.2 list=Fast-Speedtest
add address=119.18.150.8 list=Fast-Speedtest
add address=103.15.164.23 list=Fast-Speedtest
add address=103.43.148.67 list=Fast-Speedtest
add address=192.168.10.2 list=Fast-Speedtest
add address=118.179.75.213 list=Fast-Speedtest
add address=123.253.37.2 list=Fast-Speedtest
add address=182.160.96.0/24 list=Fast-Speedtest
add address=103.15.40.0/24 list=Fast-Speedtest
add address=103.213.237.62 list=Fast-Speedtest
add address=210.176.156.49 list=Fast-Speedtest
add address=210.176.156.48 list=Fast-Speedtest
add address=151.101.54.114 list=Fast-Speedtest
add address=151.101.42.114 list=Fast-Speedtest
add address=151.101.10.214 list=Fast-Speedtest
add address=151.101.26.114 list=Fast-Speedtest
add address=151.101.0.143 list=Fast-Speedtest
add address=151.101.0.84 list=Fast-Speedtest
add address=125.56.237.3 list=Fast-Speedtest
add address=104.84.156.138 list=Fast-Speedtest
add address=59.151.128.157 list=Fast-Speedtest
add address=23.219.132.176 list=Fast-Speedtest
add address=23.198.124.11 list=Fast-Speedtest
add address=23.77.26.81 list=Fast-Speedtest
add address=182.79.223.0/24 list=Fast-Speedtest
add address=23.9.187.175 list=Fast-Speedtest
add address=52.33.112.234 list=Fast-Speedtest
add address=52.41.203.109 list=Fast-Speedtest
add address=69.173.159.0/24 list=Fast-Speedtest
add address=104.79.117.49 list=Fast-Speedtest
add address=104.118.129.134 list=Fast-Speedtest
add address=104.122.15.153 list=Fast-Speedtest
add address=104.122.11.167 list=Fast-Speedtest
add address=104.122.8.110 list=Fast-Speedtest
add address=104.121.255.145 list=Fast-Speedtest
add address=speedtest.net list=Fast-Speedtest
add address=Fast-Speedtest list=Fast-Speedtest
add address=151.101.1.130 list=Fast-Speedtest
add address=184.26.196.191 list=Fast-Speedtest
add address=173.239.53.18 list=Fast-Speedtest
add address=151.101.196.64 list=Fast-Speedtest
add address=151.101.193.21 list=Fast-Speedtest
add address=151.101.10.208 list=Fast-Speedtest
add address=151.101.10.109 list=Fast-Speedtest
add address=151.101.9.108 list=Fast-Speedtest
add address=151.101.2.133 list=Fast-Speedtest
add address=151.101.2.110 list=Fast-Speedtest
add address=151.101.2.109 list=Fast-Speedtest
add address=151.101.1.186 list=Fast-Speedtest
add address=23.74.243.73 list=Fast-Speedtest
add address=34.208.20.104 list=Fast-Speedtest
add address=35.172.96.212 list=Fast-Speedtest
add address=192.229.237.182 list=Fast-Speedtest
add address=151.101.65.21 list=Fast-Speedtest
add address=151.101.129.21 list=Fast-Speedtest
add address=151.101.10.2 list=Fast-Speedtest
add address=151.101.8.81 list=Fast-Speedtest
add address=151.101.2.114 list=Fast-Speedtest
add address=128.1.97.163 list=Fast-Speedtest
add address=104.118.121.11 list=Fast-Speedtest
add address=199.232.237.51 list=Fast-Speedtest
add address=151.101.126.91 list=Fast-Speedtest
add address=151.101.114.91 list=Fast-Speedtest
add address=151.101.130.91 list=Fast-Speedtest
add address=151.101.2.91 list=Fast-Speedtest
add address=151.101.1.42 list=Fast-Speedtest
add address=182.79.164.0/24 list=Fast-Speedtest
add address=23.47.232.222 list=Fast-Speedtest
add address=52.42.104.145 list=Fast-Speedtest
add address=52.41.214.164 list=Fast-Speedtest
add address=118.215.155.65 list=Fast-Speedtest
add address=44.233.205.57 list=Fast-Speedtest
add address=35.155.65.240 list=Fast-Speedtest
add address=100.20.17.138 list=Fast-Speedtest
add address=202.150.221.0/24 list=Fast-Speedtest
add address=182.79.161.0/24 list=Fast-Speedtest
add address=182.79.245.0/24 list=Fast-Speedtest
add address=182.79.160.0/22 list=Fast-Speedtest
add address=182.79.164.0/22 list=Fast-Speedtest
add address=45.57.50.0/24 list=Fast-Speedtest
add address=45.57.51.0/24 list=Fast-Speedtest
add address=108.159.58.0/24 list=Fast-Speedtest
add address=69.173.158.0/24 list=Fast-Speedtest
add address=182.79.164.2 list=Fast-Speedtest
add address=182.79.164.165 list=Fast-Speedtest
add address=182.79.164.55 list=Fast-Speedtest
add address=182.79.164.6 list=Fast-Speedtest
add address=182.79.161.233 list=Fast-Speedtest
add address=45.57.51.140 list=Fast-Speedtest
add address=182.79.223.234 list=Fast-Speedtest
add address=45.57.50.142 list=Fast-Speedtest
add address=182.79.223.230 list=Fast-Speedtest
add address=45.57.51.146 list=Fast-Speedtest
add address=45.57.50.150 list=Fast-Speedtest
add address=45.57.51.153 list=Fast-Speedtest
add address=23.246.55.163 list=Fast-Speedtest
add address=45.57.51.142 list=Fast-Speedtest
add address=49.44.61.0/24 list=Fast-Speedtest
add address=103.87.204.0/22 list=Fast-Speedtest
add address=23.246.0.0/18 list=Fast-Speedtest
add address=45.57.0.0/17 list=Fast-Speedtest
add address=37.77.184.0/21 list=Fast-Speedtest
add address=64.120.128.0/17 list=Fast-Speedtest
add address=108.175.32.0/20 list=Fast-Speedtest
add address=185.2.220.0/22 list=Fast-Speedtest
add address=185.9.188.0/22 list=Fast-Speedtest
add address=35.0.0.0/8 list=Fast-Speedtest
add address=182.79.0.0/16 list=Fast-Speedtest
add address=52.35.0.0/16 list=Fast-Speedtest
add address=23.246.0.0/16 list=Fast-Speedtest
add address=37.77.184.0/21 list=Fast-Speedtest
add address=45.57.0.0/17 list=Fast-Speedtest
add address=64.120.128.0/17 list=Fast-Speedtest
add address=66.197.128.0/17 list=Fast-Speedtest
add address=185.2.220.0/22 list=Fast-Speedtest
add address=185.9.188.0/22 list=Fast-Speedtest
add address=198.9.188.0/22 list=Fast-Speedtest
add address=198.38.96.0/19 list=Fast-Speedtest
add address=182.79.223.0/24 list=Fast-Speedtest
add address=182.79.164.0/24 list=Fast-Speedtest
add address=61.8.176.0/20 list=Fast-Speedtest
add address=199.58.164.0/22 list=Fast-Speedtest
add address=131.161.168.0/22 list=Fast-Speedtest
add address=103.101.59.0/24 list=Fast-Speedtest
add address=103.102.42.0/23 list=Fast-Speedtest
add address=23.77.0.0/18 list=Fast-Speedtest
add address=23.246.0.0/18 list=Fast-Speedtest
/ip firewall mangle
add action=mark-packet chain=forward dst-address-list=Fast-Speedtest new-packet-mark=fast-upload passthrough=no src-address-list=Client-IP
add action=mark-packet chain=forward dst-address-list=Client-IP new-packet-mark=fast-download passthrough=no src-address-list=Fast-Speedtest
/queue type
add kind=pcq name=fast-upload pcq-classifier=src-address pcq-dst-address6-mask=64 pcq-rate=30M pcq-src-address6-mask=64
add kind=pcq name=fast-download pcq-classifier=dst-address pcq-dst-address6-mask=64 pcq-rate=30M pcq-src-address6-mask=64
/queue simple
add name="Fast-Upload-bdix" dst=HTL-BDIX packet-marks=fast-upload queue=fast-upload/fast-download target=""
add name="Fast-Download-bdix" dst=HTL-BDIX packet-marks=fast-download queue=fast-upload/fast-download target=""
/queue simple
add name="Fast-Upload" dst=HTL-INT packet-marks=fast-upload queue=fast-upload/fast-download target=""
add name="Fast-Download" dst=HTL-INT packet-marks=fast-download queue=fast-upload/fast-download target=""